Antwort What are the 4 components of identity access management? Weitere Antworten – What are the 4 pillars of IAM
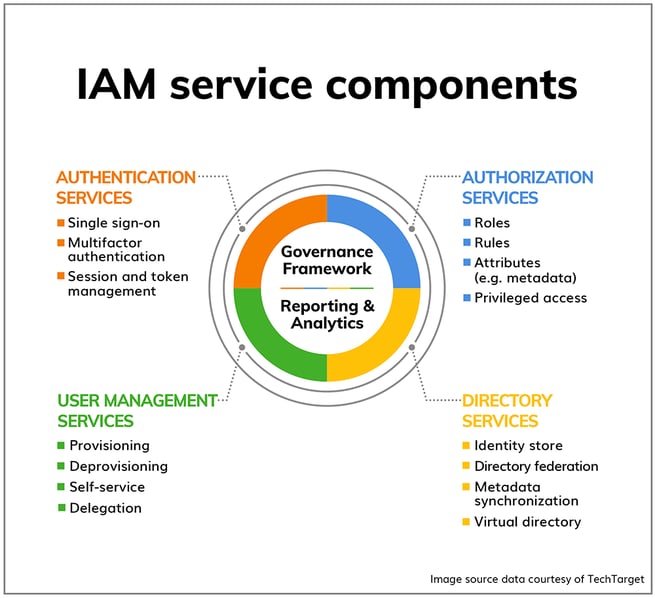
IAM is an overarching framework built using four core pillars: IGA, AM, PAM and ADmgmt.IAM consists of four main components: Authentication, Authorization, Administration, and Auditing and Reporting. Advanced tools like Single Sign-On (SSO), Multifactor Authentication (MFA), and Identity Governance and Administration (IGA) are employed in IAM to enhance security and user experience.Broadly speaking, there are four key aspects to IdAM solutions that ensure only validated users can access enterprise data and resources.
- User Management.
- Central User Repository.
- Authentication.
- Authorization.
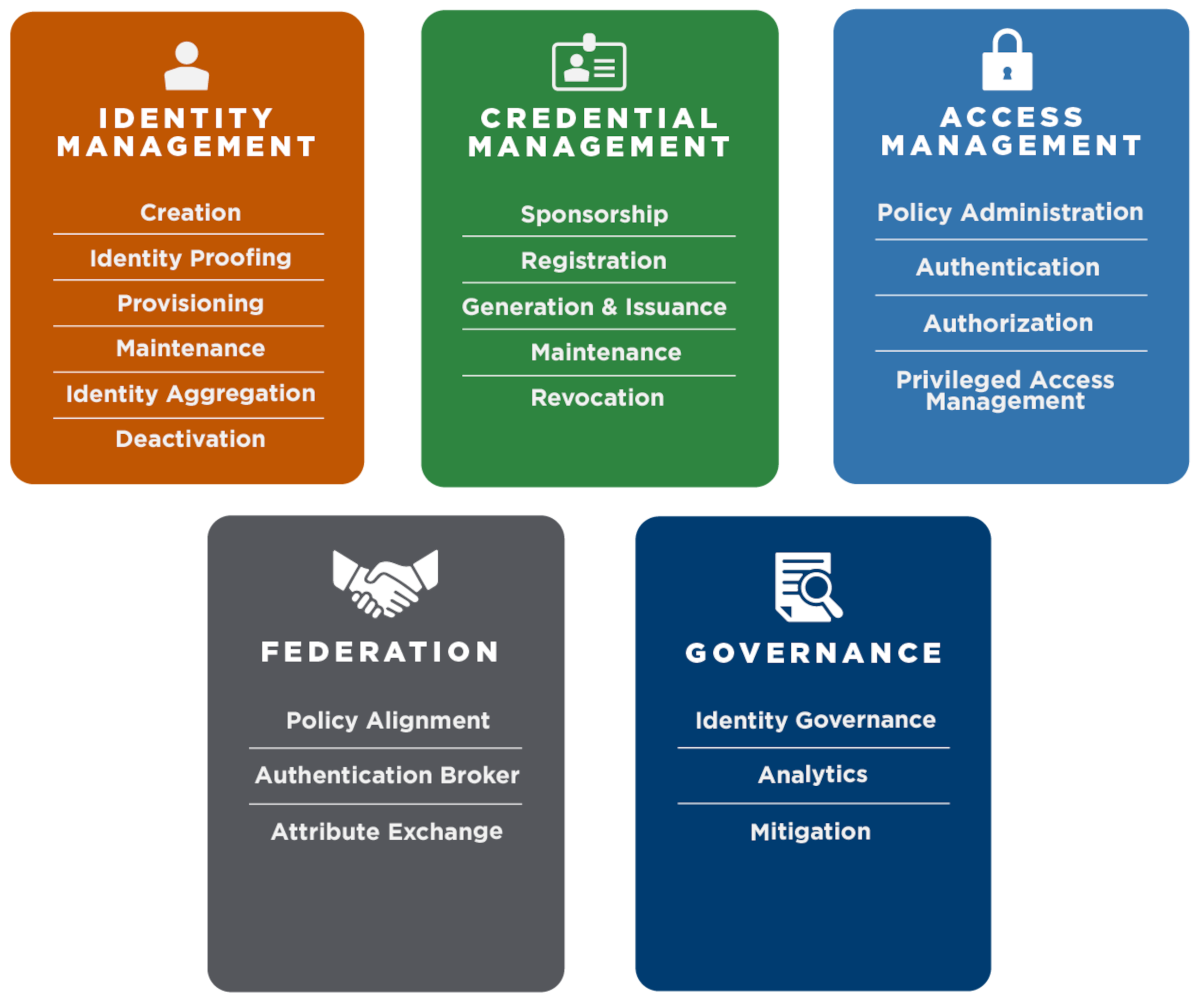
What are the components of identity management : IAM components can be classified into four major categories: authentication, authorisation, user management, and central user repository. Authentication is the module through which a user provides sufficient credentials to gain initial access to an application system of a particular resource.
What are the 3 A’s of IAM
Authentication can take place as an individual process or can be combined with authorization and accounting. An effective password strategy is the key to an effective authentication process. These include the frequent change of passwords, a strict password policy and processes that protects data from outsiders.
What are the stages of IAM : The IAM lifecycle consists of four main stages: provisioning, authentication, authorization, and deprovisioning. Each stage has its own challenges and opportunities for improvement. Provisioning refers to the creation and assignment of identities and credentials for new users and systems.
Identity and access management (IAM) is a framework of business processes, policies and technologies that facilitates the management of electronic or digital identities. With an IAM framework in place, information technology (IT) managers can control user access to critical information within their organizations.
Five Pillars of Identity. German Psychologist Hilarion Petzold conceptualized identity into five pillars: Mind and Body; Relationships; Work and Hobbies; Material Safety; and Values. As depicted in the image below, the loss of one pillar can cause our overall identity to be eroded.
What are the five components of identity
Adams and Marshall (1996) established that identity formation provides five functions: a structure and order to self-knowledge; a sense of consistency and coherence to beliefs, goals, and self-knowledge; a sense of continuity for one's history and future; goals and direction; a sense of personal control of their …IAM policies define permissions for an action regardless of the method that you use to perform the operation. For example, if a policy allows the GetUser action, then a user with that policy can get user information from the AWS Management Console, the AWS CLI, or the AWS API.IAM strategies ensure that those who have access to the company's IT environment are people who comply with the company's requirements; that is, that they are following its policies and are part of it.
Eight major social identities, often referred to as “the big eight,” are commonly used to describe how a person categorizes themselves and others — ability, age, ethnicity, gender, race, religion, sexual orientation and socioeconomic status.
What are the 4 dimensions of identity : They unpack both Commitment and Exploration, each into two forms, and they distinguish the following four identity dimensions: Commitment Making, Identification with Commitment, Exploration in Breadth, and Exploration in Depth.
How to do an IAM audit : Identity and Access Management audit checklist
- Focus on your security policy.
- Assign responsibilities clearly.
- Review privileged user credentials.
- Schedule user reviews to clean up IAM systems.
- Apply segmentation of duties where appropriate.
- Clean up unused accounts.
- Review compliance documentation.
Which IAM tool is best
Top 10 Identity and Access Management (IAM) Software
- Microsoft Entra ID.
- JumpCloud.
- Okta Workforce Identity.
- Salesforce Platform.
- Cisco Duo.
- AWS Vertrified Access.
- IBM Security Verify.
- Oracle Identity Cloud Service.

KPIs are a means of measuring IAM performance in order to keep track of and understand IAM effectiveness, and identify potential areas for improvement. Remember that once identified, more in-depth information and action-oriented insights are required to actually improve the identified issue.Workflows uses Identity and Access Management (IAM) to control which authenticated users and service accounts can perform which actions. Before you begin authenticating and authorizing access to your Workflows resources, make sure you understand the basic concepts of IAM.
What are the 5 principles of identity : It is based on five principles: Emergence, Positionality, Indexicality, Relationality and Partialness. Identity is produced by linguistic resources that are broad and flexible – labels, stances, styles, and even languages and varieties.
